GroupWise 18 WebAccess on Windows Server
Here is a list of things required to get GroupWise WebAccess 18 running on a Windows Server. The architecture is different than previous versions of GroupWise, the main difference being that it uses Apache Tomcat instead of IIS for the web services. This outlines the challenges associated with the change.
If you'd like to, you can reference this Micro Focus TID, however please note that it contains mistakes in syntax and general inaccuracies that I will not go into detail here. https://support.microfocus.com/kb/doc.php?id=7022859
Potential Challenges to Overcome:
- IIS is disabled, and instead Apache Tomcat is used
- Certificates are not transferred to Apache Tomcat
- Apache Tomcat by default is configured to use the tomcat keystore and the NIO directive
- Default Weak TLS Versions with Apache Tomcat
- Uninstalling / Reinstalling GroupWise 18.x Webaccess considerations
- Patching / Updating Webaccess overwrites tomcat/apache config file
Change from IIS to Tomcat Apache
Understand that the GroupWise WebAccess 18.x installation process will disable IIS and install an Apache Tomcat service that runs WebAccess in its entirety. If you're not expecting this, you can expect some frustration as you're trying to figure out what's going on.
Certificates are not Transferred to Apache Tomcat service
By default, the Apache Tomcat service is configured with a self signed certificate. So even if you have certificates installed with IIS, you will see that WebAccess 18.x is using self signed certificates. To my knowledge the GroupWise WebAccess installation program does not even attempt to transfer the certificate. Understanding this is critical to moving past this issue and getting up and running with real 3rd party certificates.
Apache Tomcat Configuration File
The Apache Tomcat services are mostly defined by the file server.xml that is located in C:\Novell\GroupWise\Tomcat\conf\
C:\Novell\GroupWise\Tomcat\conf\server.xml
Patching / Updating Webaccess overwrites tomcat/apache config file
You'll be frustrated to find out that when you apply a patch to WebAccess (For example, 18.1.x upgrading to 18.2.1), your customized server.xml file will likely be wiped out and a default configuration file will be installed, resetting the security back to a terrible state. Furthermore, it doesn't make a backup for you. You'll want to make a backup of the server.xml file before you apply any patches.
Apache Tomcat keystore vs Certificate File directives
By default, GroupWise WebAccess 18 is installed to use what is called the "NIO" directive. There are two different directives that can be used, the NIO and the APR directives.
The NIO Directives can be identified by this line in the server.xml file
<Connector port="443" protocol="org.apache.coyote.http11.Http11NioProtocol"The APR Directives can be identified by this line in the server.xml file
<Connector port="443" protocol="org.apache.coyote.http11.Http11AprProtocol"
The Default directive, NIO, uses the Tomcat Keystore for certificate management. This is a more complicated method and can be extremely cumbersome. It is much easier to use the APR directive, which uses the standard certificate, key file, and intermediate certificate from the 3rd party.
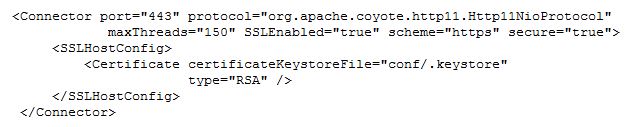
Below is what the default directives in the server.xml file look like after a GroupWise WebAccess 18 installation. You can see reference to the NIO directive and also reference to a keystore. Just understand that the keystore is where the self signed certificate was installed into.
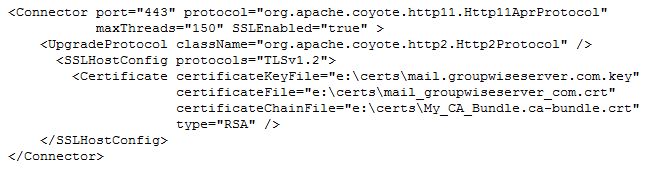
Below is the optimal configuration for the server.xml configuration file using the APR directive. Please note the following:
- The NIO section above must be commented out or removed from the server.xml file.
- The APR section must be enabled. By default it is commented out.
- The image shown has been further customized from the default settings. By using the default APR configuration, it's very unlikely that the services will load. More on this later.
- You must configure the server.xml file with your own certificate file, key file, and intermediate certificate file from your certificate vendor.
Steps to get the APR Directive working with Apache Tomcat
The default APR directive is incomplete and most likely will not work in its current state.
- Un-comment the APR section after disabling the NIO section.
- Inside the "Certificate" Directive, Edit the "CertificateKeyFile" part to include the path and filename to your key file
- Edit the "CertificateFile" part to include the path and filename to your certificate file.
- Add another directive for the Intermediate Certificate and include the pathname. It should be within the bounds of the "Certificate" directive. The parameter is "CertificateChainFile", and include the path and filename to the intermediate certificate from your provider.
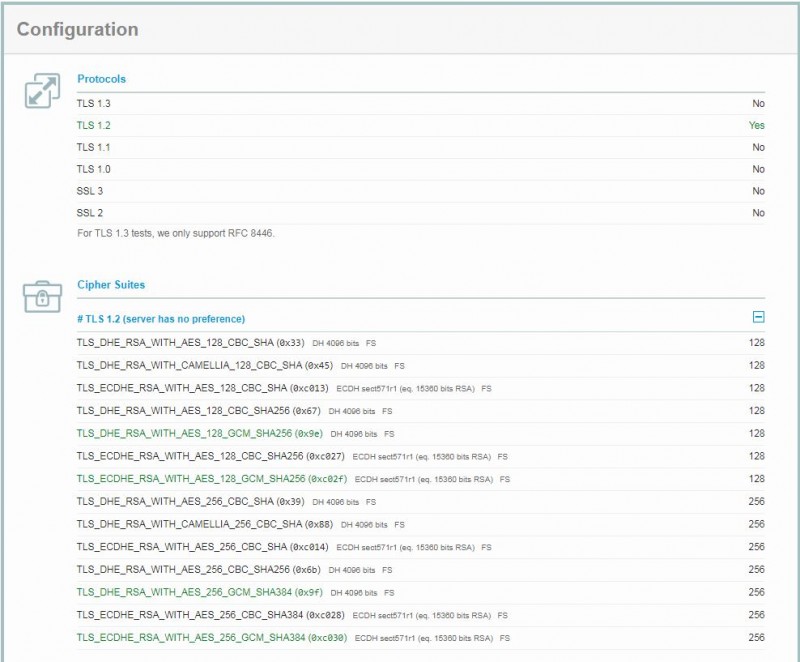
Default Weak TLS Versions with Apache Tomcat
By Default, TLS 1.0, TLS 1.1, and TLS1.2 are enabled when you install GroupWise WebAccess 18.x. This is not desirable due to security concerns and vulnerabilities. The way to overcome this is to add the following parameter to the APR directive in the server.xml file:
<SSLHostConfig protocols="TLSv1.2">
This parameter will disable TLS v1.0 and TLS v1.1 and only allow connections using TLS v1.2
Uninstalling / Reinstalling GroupWise WebAccess
One thing that can be extremely frustrating is if you decide you need/want to just start over from scratch, and then uninstall and reinstall GroupWise WebAccess. There are many things that happen behind that scenes and there is no feedback or confirmation of any of the actions. So this details some additional information you need to know should you choose start over.
Installing GroupWise WebAccess
When you install GroupWise WebAccess, these are the main things that happen:
- "GroupWise WebAccess" is added to your Programs and Features list in the Windows Control Panel.
- "Apache Tomcat for GroupWise" is added to your Programs and Features list in the Windows Control Panel.
- A Windows service called "Apache Tomcat 9.0 Tomcat9" is created.
Uninstalling GroupWise WebAccess
When you uninstall GroupWise WebAccess, it does not automatically reverse all of the above actions. It only removes the "GroupWise WebAccess" from the list of installed programs. In order to fully uninstall GroupWise WebAccess to start over, you must do the following:
- Uninstall GroupWise WebAccess from the Programs and Features list.
- Uninstall "Apache Tomcat 9.0 Tomcat 9" from the Programs and Features list. This "Should remove the Apache Tomcat service as well."
- You may want to remove the folder c:\Novell\Groupwise\Tomcat and c:\Novell\WebAccess (Use caution).
Download a ready to go server.xml file
You can download the following server.xml file and use the syntax to get GroupWise WebAccess working on your system. Just edit the path and certificate filenames in the "Certificate" section. Lines 99, 100, and 101 should be all you need to modify.
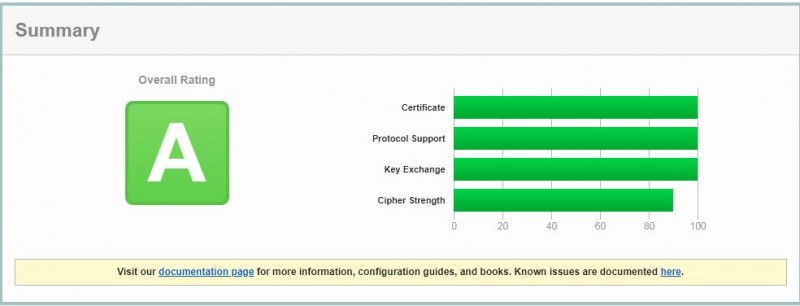
Security Results in Action
Below is a screenshot from SSL Labs SSL Server test. Note that the server received an "A" grade and I can also confirm that only TLS 1.2 is enabled.